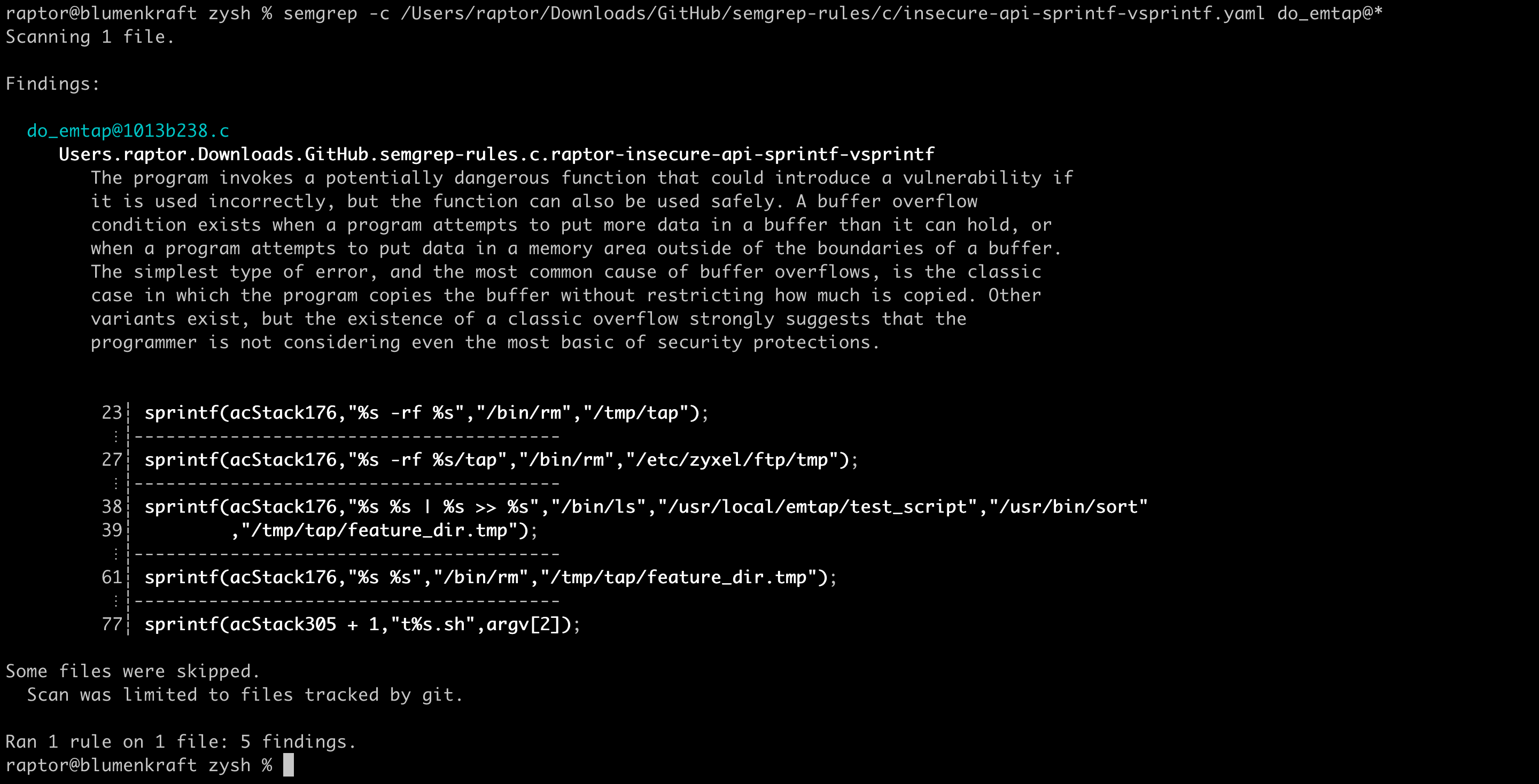
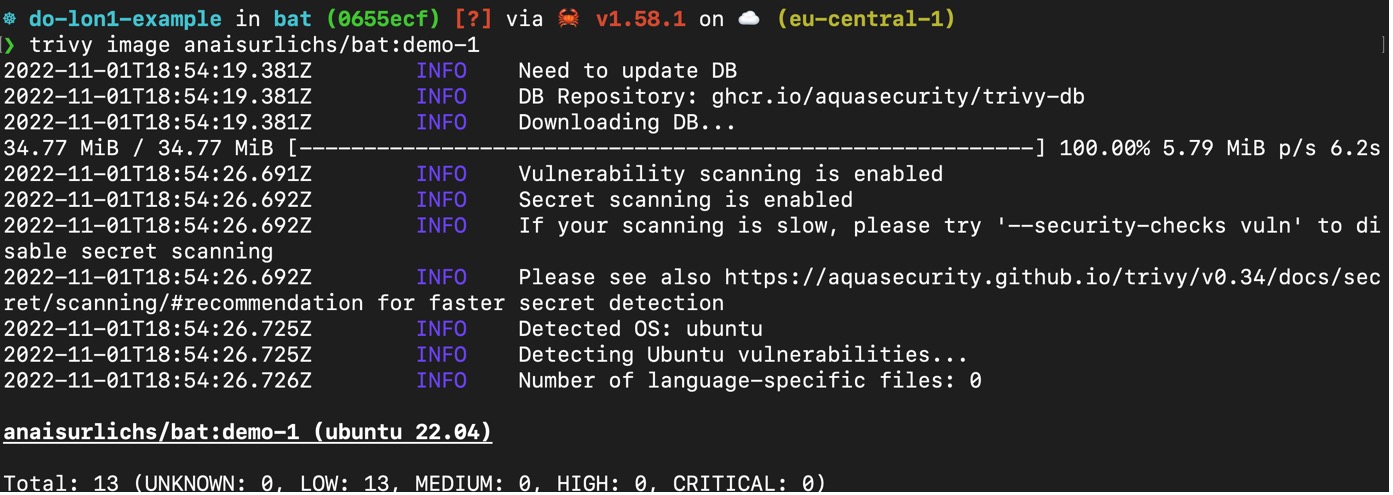
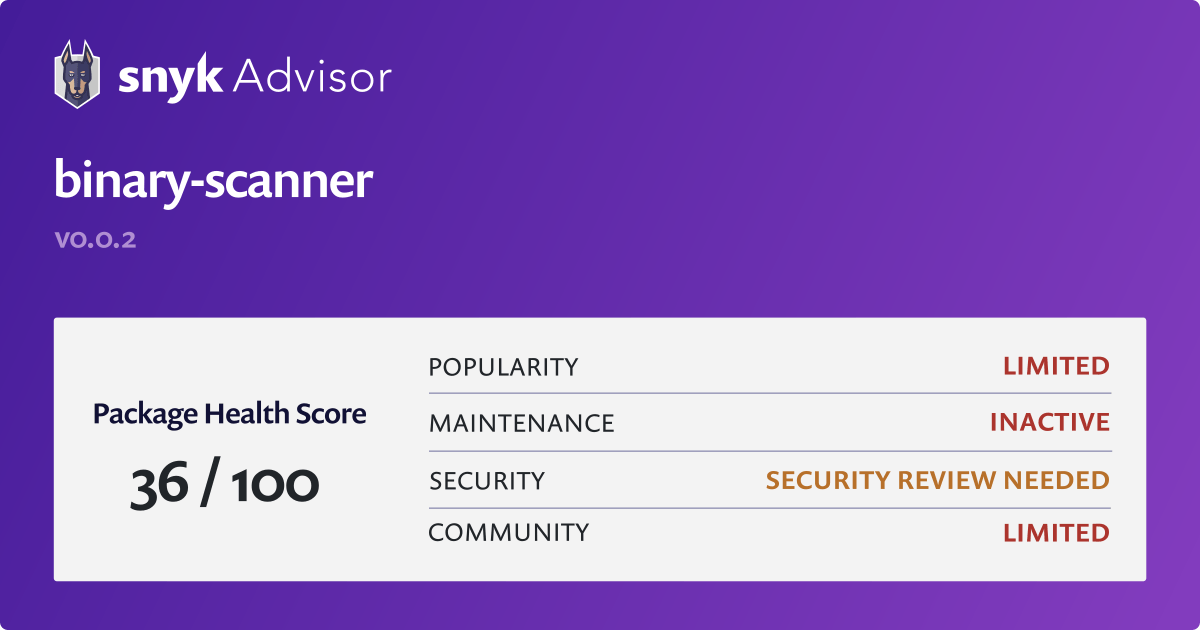
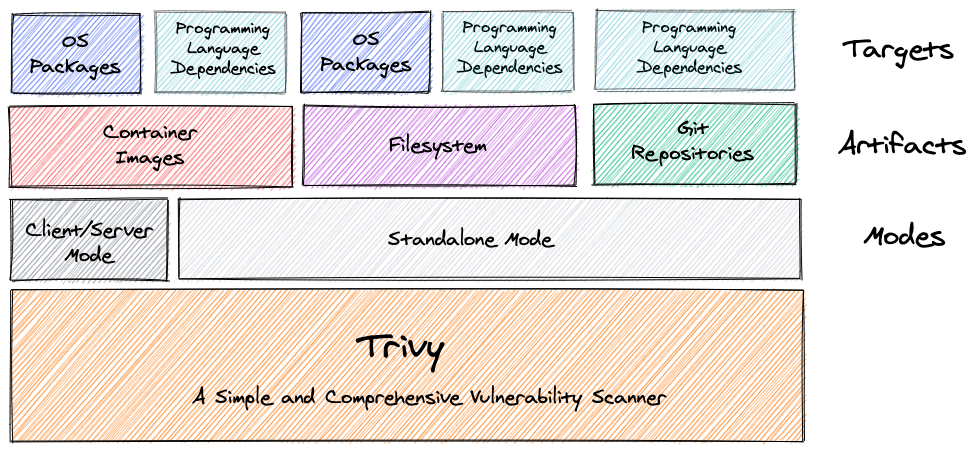
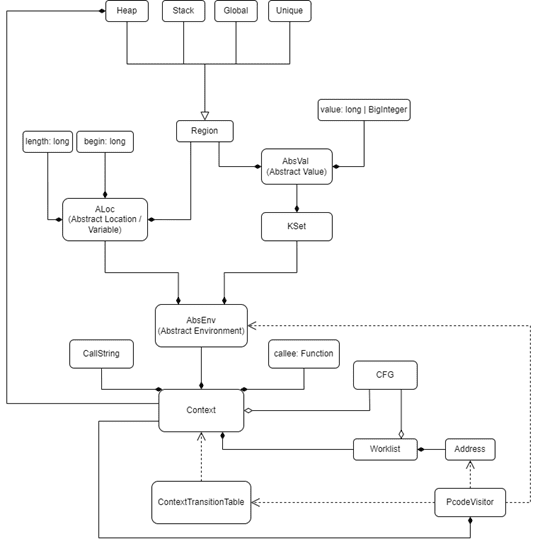
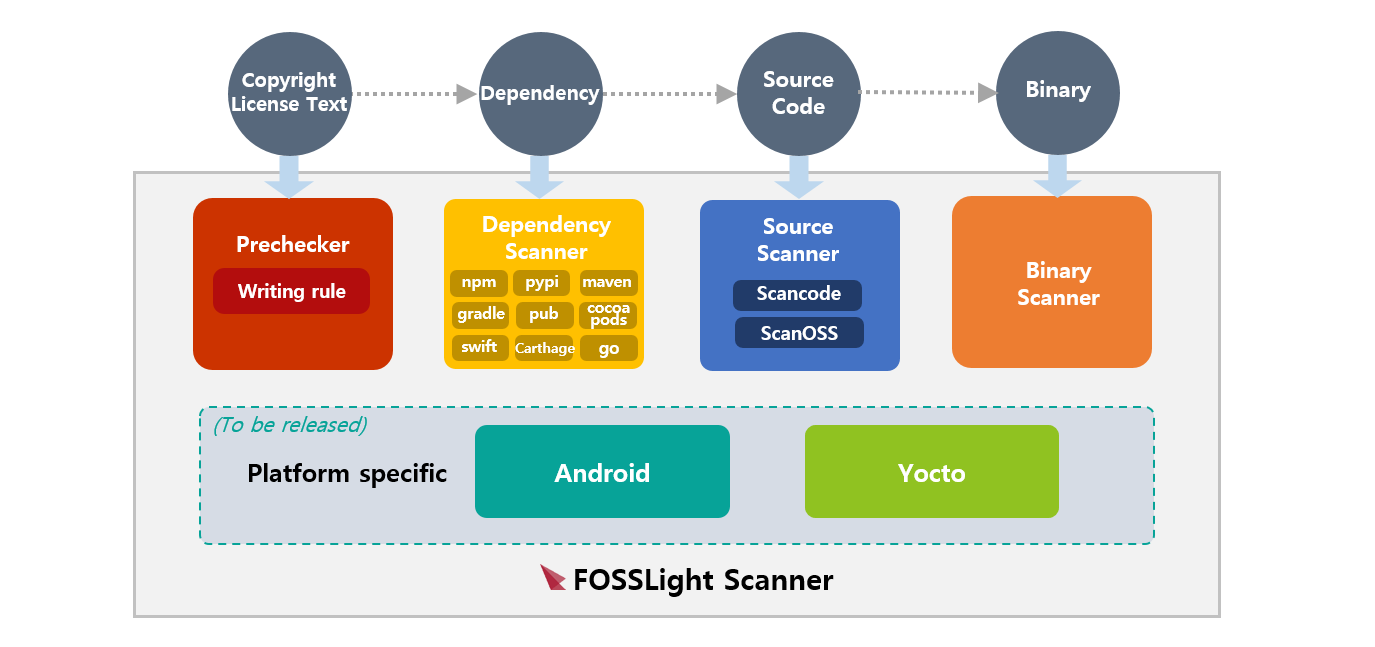
Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog

Vulnerability Scanner Showdown: AppDetectivePro 5.4.6 vs. AuditPro Enterprise 4.0 | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More

Binary Code Encryption Stock Photo - Download Image Now - Bar Code Reader, Vulnerability, Computer - iStock
GitHub - intel/cve-bin-tool: The CVE Binary Tool helps you determine if your system includes known vulnerabilities. You can scan binaries for over 200 common, vulnerable components (openssl, libpng, libxml2, expat and others),