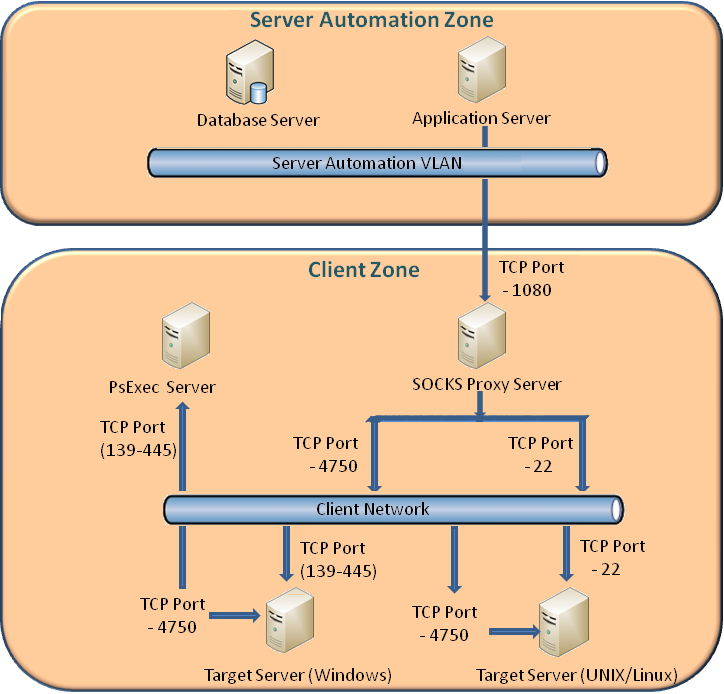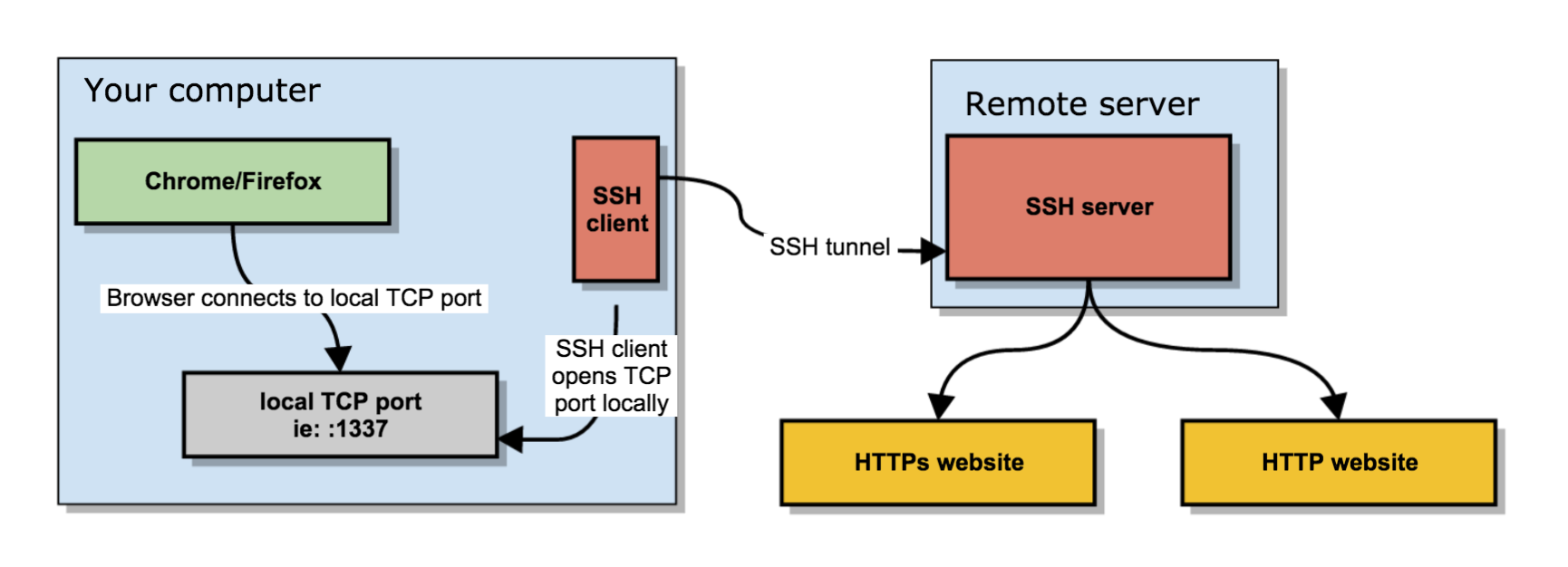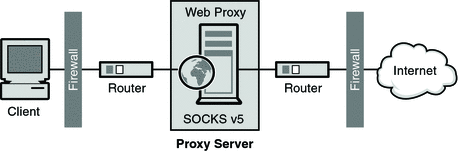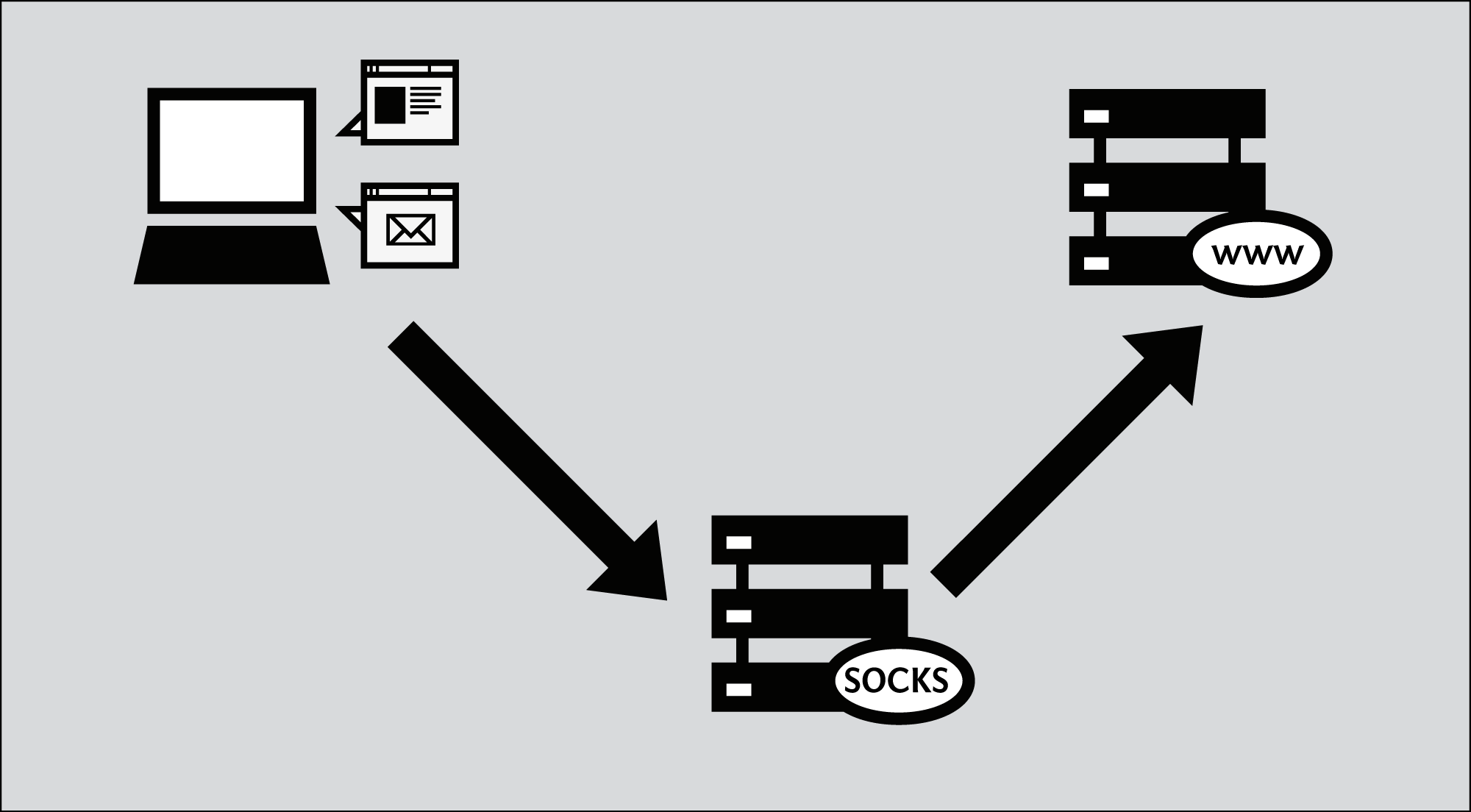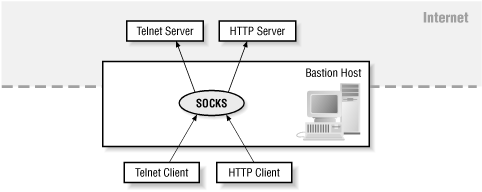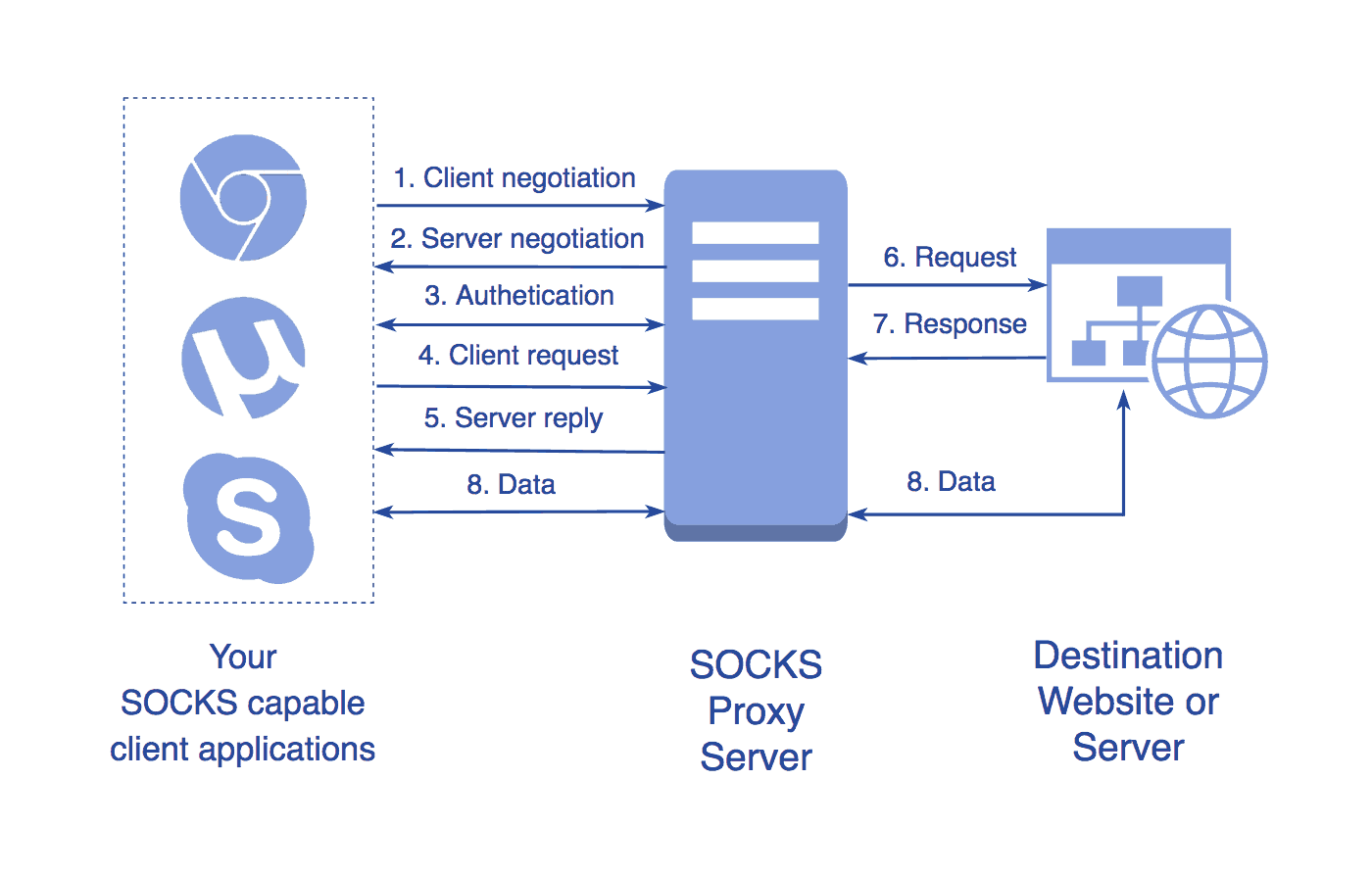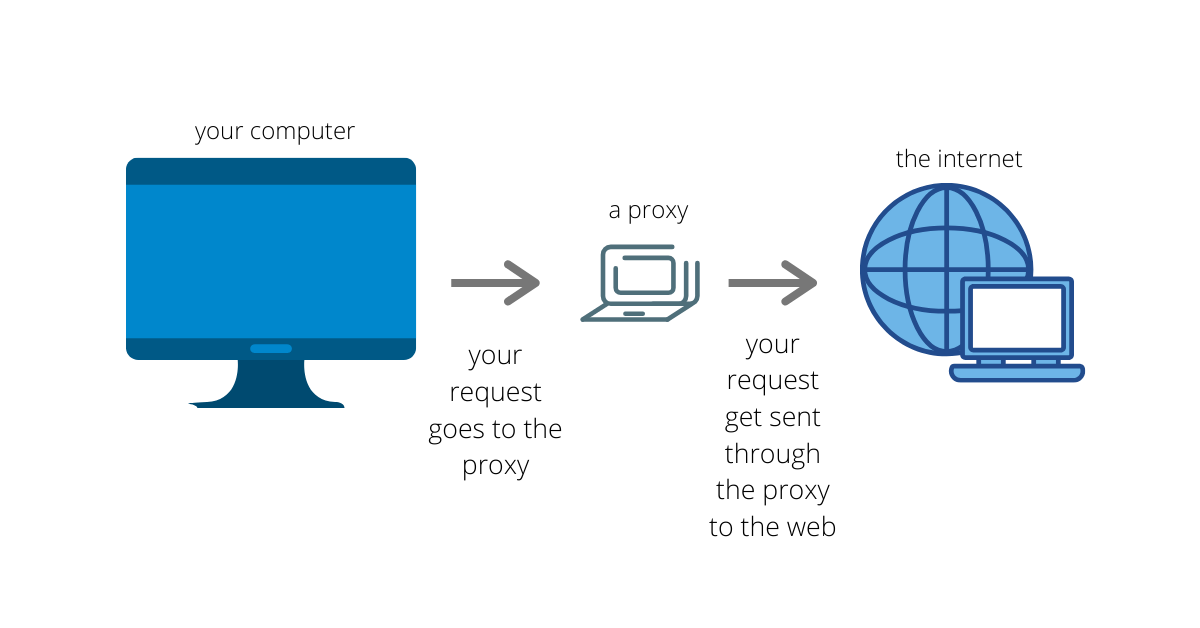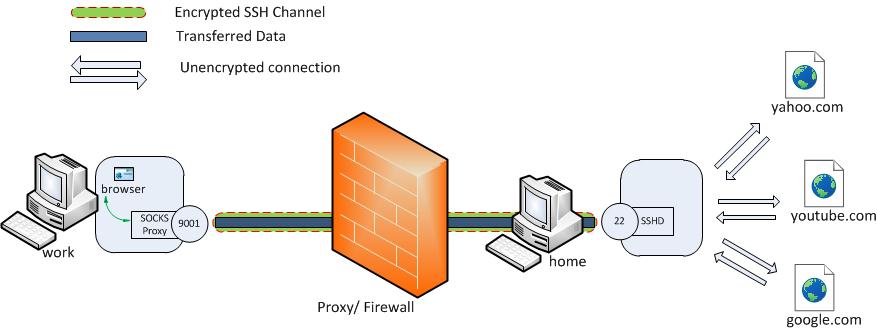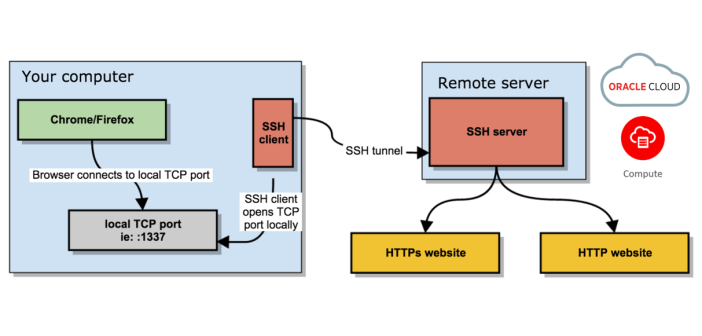
Secure browsing using a local SOCKS proxy server (on desktop or mobile) and an always free OCI compute instance as SSH server
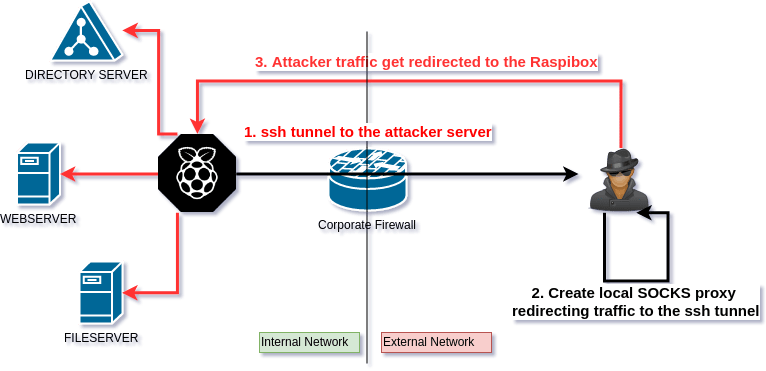
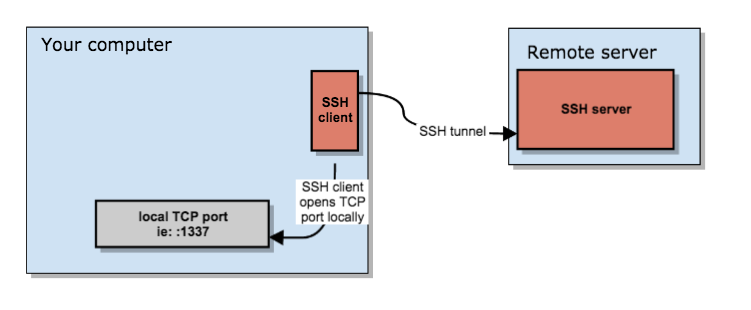
Proxy Windows Tooling via SOCKS. Leveraging SOCKS to proxy tools from a… | by Nick Powers | Posts By SpecterOps Team Members
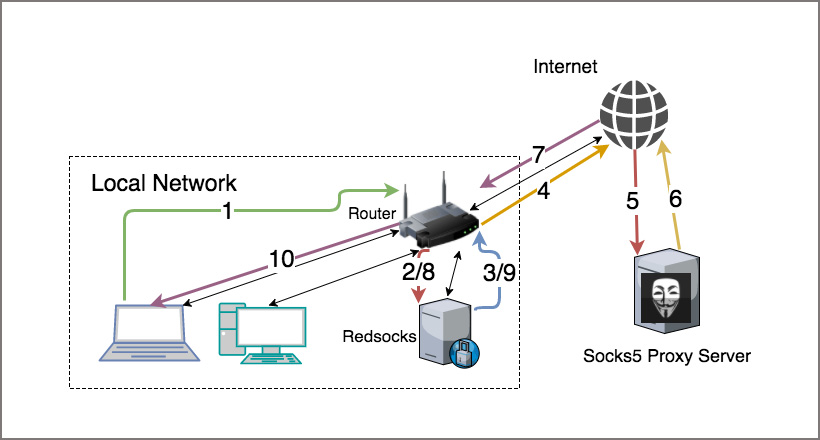
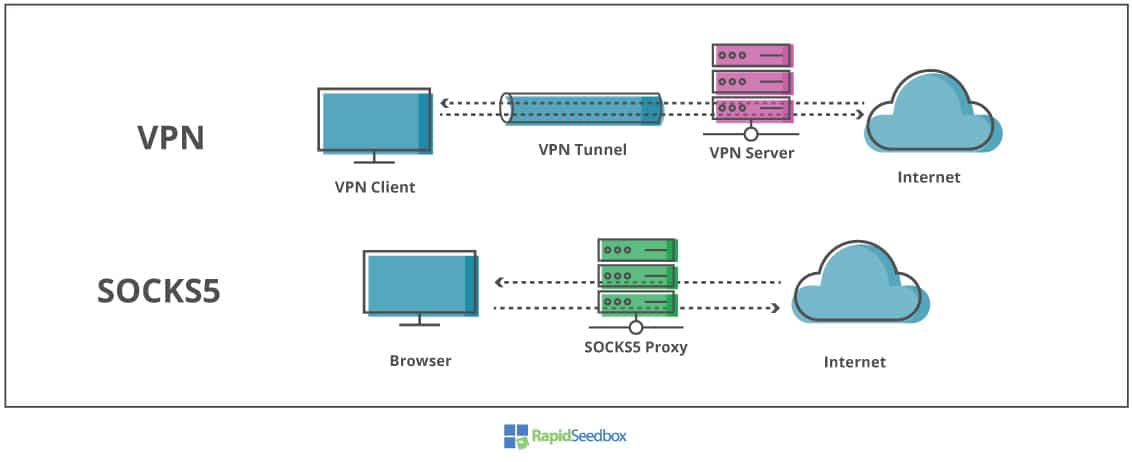
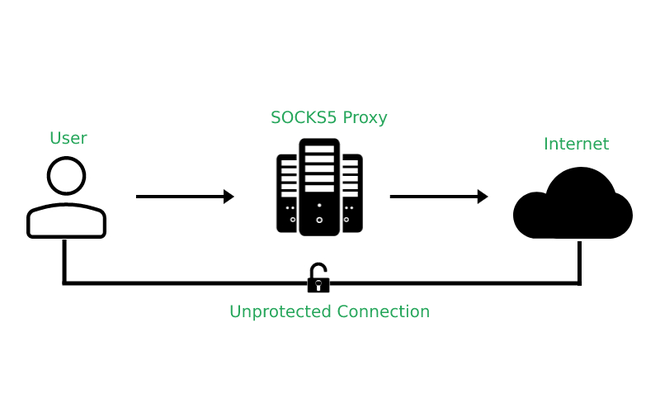
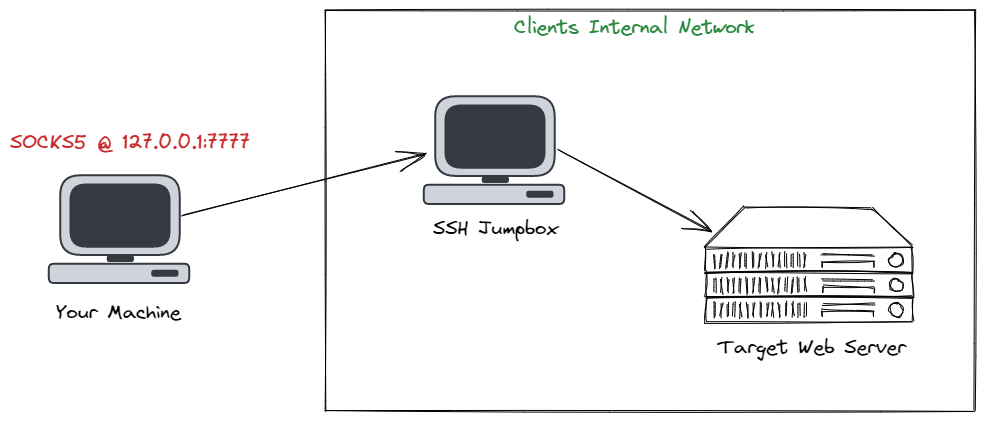
How to Route All Network Traffic from your LAN securely through a SOCKS5 proxy + SSH Tunnel + Redsocks | DNSFLEX